CKA [Installation] – Ubuntu 从0架设,架设API Server
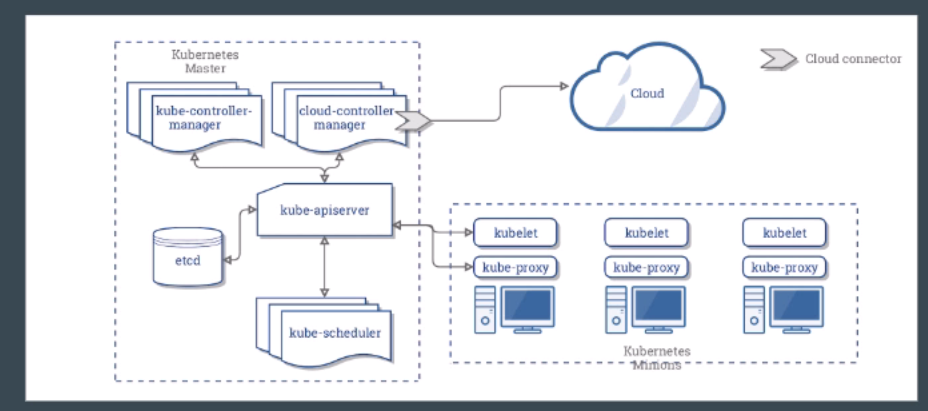
这个教程里我们需要架设kube-apiserver, 从以上的架构图你可以看到,所有的kubernetes的设定都会把数据给保存在ETCD内,所以架设kube-apiserver之前需要完成ETCD的架设先。
由于kube-apiserver拥有很多命令行,你可以查看官方文档:https://kubernetes.io/docs/reference/command-line-tools-reference/kube-apiserver/
1. 去到binary 的文件夹,然后把kube-apiserver 给拷贝到 /usr/local/bin , 如果你还没下载k8s binary的话就需要去到这个文章先:https://www.pangzai.win/cka-installation-ubuntu-%e4%bb%8e0%e6%9e%b6%e8%ae%be%ef%bc%8c%e4%b8%8b%e8%bd%bdkubernetes-binary-files/
cd /root/binaries/kubernetes/server/bin/cp kube-apiserver /usr/local/bin/2. 在Terminal 内设置Public Ip
SERVER_IP=206.189.40.75 (change this to your IP)echo $SERVER_IP3. 生成用于 CSR 创建的配置文件
cd /root/certificatescat <<EOF | sudo tee api.conf
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = kubernetes
DNS.2 = kubernetes.default
DNS.3 = kubernetes.default.svc
DNS.4 = kubernetes.default.svc.cluster.local
IP.1 = 127.0.0.1
IP.2 = ${SERVER_IP}
IP.3 = 10.32.0.1
EOF4. 为API Server 生成 certificate
{
openssl genrsa -out kube-api.key 2048
openssl req -new -key kube-api.key -subj "/CN=kube-apiserver" -out kube-api.csr -config api.conf
openssl x509 -req -in kube-api.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out kube-api.crt -extensions v3_req -extfile api.conf -days 1000
}5. 为Service Account生成certificate
{
openssl genrsa -out service-account.key 2048
openssl req -new -key service-account.key -subj "/CN=service-accounts" -out service-account.csr
openssl x509 -req -in service-account.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out service-account.crt -days 100
}6. Copy certificate 文件到 /var/lib/kubernetes 目录
mkdir /var/lib/kubernetescp etcd.crt etcd.key ca.crt kube-api.key kube-api.crt service-account.crt service-account.key /var/lib/kubernetesls /var/lib/kubernetes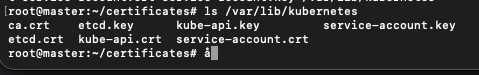
7. 创建加密密钥和配置
ENCRYPTION_KEY=$(head -c 32 /dev/urandom | base64)cat > encryption-at-rest.yaml <<EOF
kind: EncryptionConfig
apiVersion: v1
resources:
- resources:
- secrets
providers:
- aescbc:
keys:
- name: key1
secret: ${ENCRYPTION_KEY}
- identity: {}
EOFcp encryption-at-rest.yaml /var/lib/kubernetes/encryption-at-rest.yaml8. 创建 Systemd service file
cat <<EOF | sudo tee /etc/systemd/system/kube-apiserver.service
[Unit]
Description=Kubernetes API Server
Documentation=https://github.com/kubernetes/kubernetes
[Service]
ExecStart=/usr/local/bin/kube-apiserver \
--advertise-address=${SERVER_IP} \
--allow-privileged=true \
--authorization-mode=Node,RBAC \
--client-ca-file=/var/lib/kubernetes/ca.crt \
--enable-admission-plugins=NamespaceLifecycle,NodeRestriction,LimitRanger,ServiceAccount,DefaultStorageClass,ResourceQuota \
--enable-bootstrap-token-auth=true \
--etcd-cafile=/var/lib/kubernetes/ca.crt \
--etcd-certfile=/var/lib/kubernetes/etcd.crt \
--etcd-keyfile=/var/lib/kubernetes/etcd.key \
--etcd-servers=https://127.0.0.1:2379 \
--kubelet-client-certificate=/var/lib/kubernetes/kube-api.crt \
--kubelet-client-key=/var/lib/kubernetes/kube-api.key \
--service-account-key-file=/var/lib/kubernetes/service-account.crt \
--service-cluster-ip-range=10.32.0.0/24 \
--tls-cert-file=/var/lib/kubernetes/kube-api.crt \
--tls-private-key-file=/var/lib/kubernetes/kube-api.key \
--requestheader-client-ca-file=/var/lib/kubernetes/ca.crt \
--service-node-port-range=30000-32767 \
--audit-log-maxage=30 \
--audit-log-maxbackup=3 \
--audit-log-maxsize=100 \
--audit-log-path=/var/log/kube-api-audit.log \
--bind-address=0.0.0.0 \
--event-ttl=1h \
--service-account-key-file=/var/lib/kubernetes/service-account.crt \
--service-account-signing-key-file=/var/lib/kubernetes/service-account.key \
--service-account-issuer=https://${SERVER_IP}:6443 \
--encryption-provider-config=/var/lib/kubernetes/encryption-at-rest.yaml \
--v=2
Restart=on-failure
RestartSec=5
[Install]
WantedBy=multi-user.target
EOF8. 启动 kube-apiserver service
systemctl start kube-apiserversystemctl enable kube-apiserversystemctl status kube-apiserver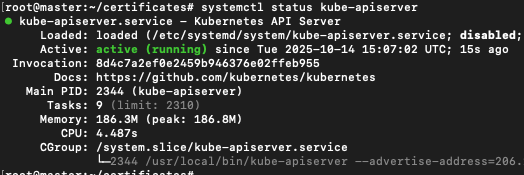
![]()
Facebook评论