AWS 使用console创建IPv6 EKS集群,配置VPC-CNI Role
【Console – 创建集群】
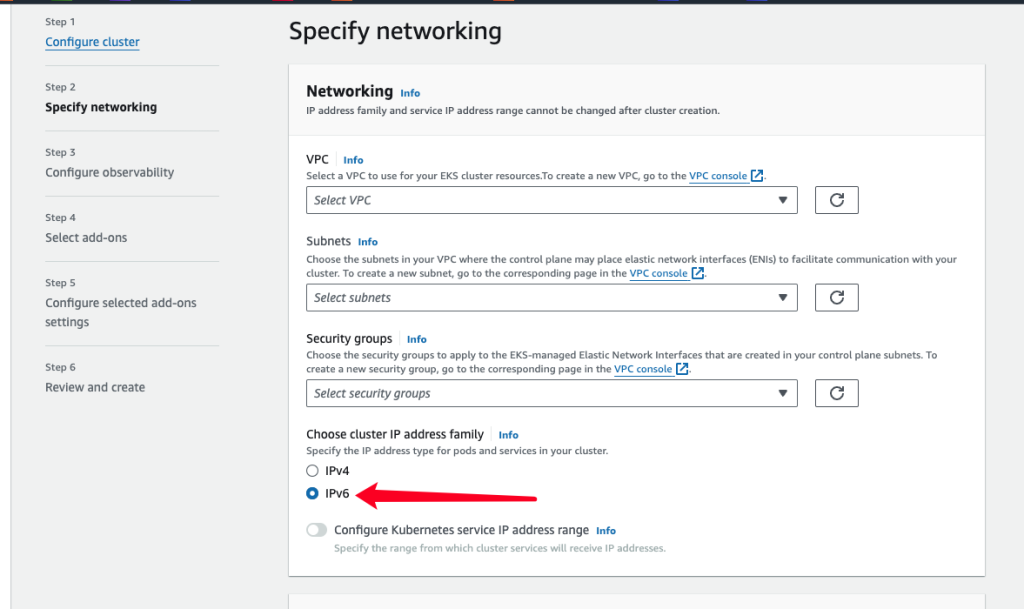
在networking当中选择IPv6, subnet和VPC就选择你创建好的,记得设定好IPv6 CIDR
参考文章:https://www.pangzai.win/aws-%e5%88%9b%e5%bb%baeks%e9%9b%86%e7%be%a4/
【配置VPC CNI】
参考文档:https://docs.aws.amazon.com/eks/latest/userguide/cni-iam-role.html
创建好了集群之后就需要为VPC CNI 创建Role,然后绑定
- 创建集群IAM OIDC身份提供商, 如果你已经创建了就无需再创建
eksctl utils associate-iam-oidc-provider --cluster yourClusterName --approve2. 创建好OIDC了之后就获取OIDC的ARN
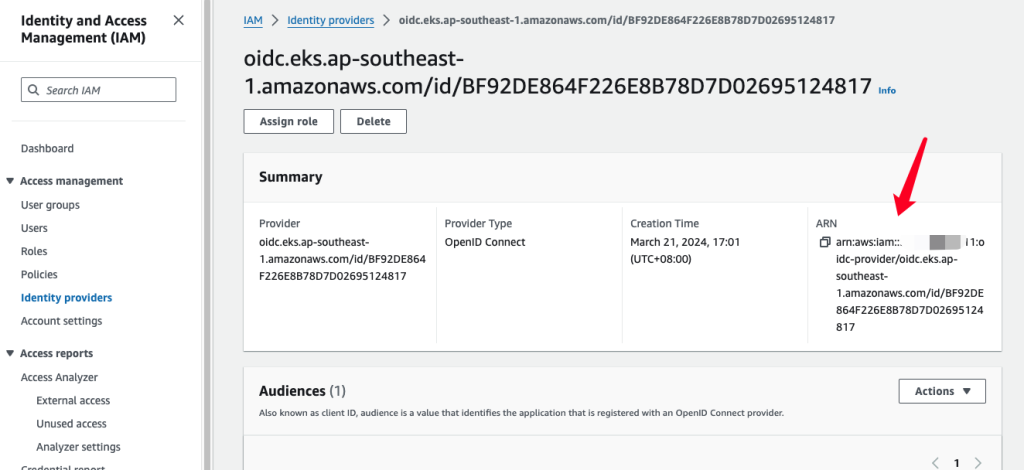
3. 创建新Role,选择custom trust policy,把OIDC ARN给换成刚刚创建好的,StringEquals当中的信息也要改成创建好的OIDC ID, 然后next到完就创建好了
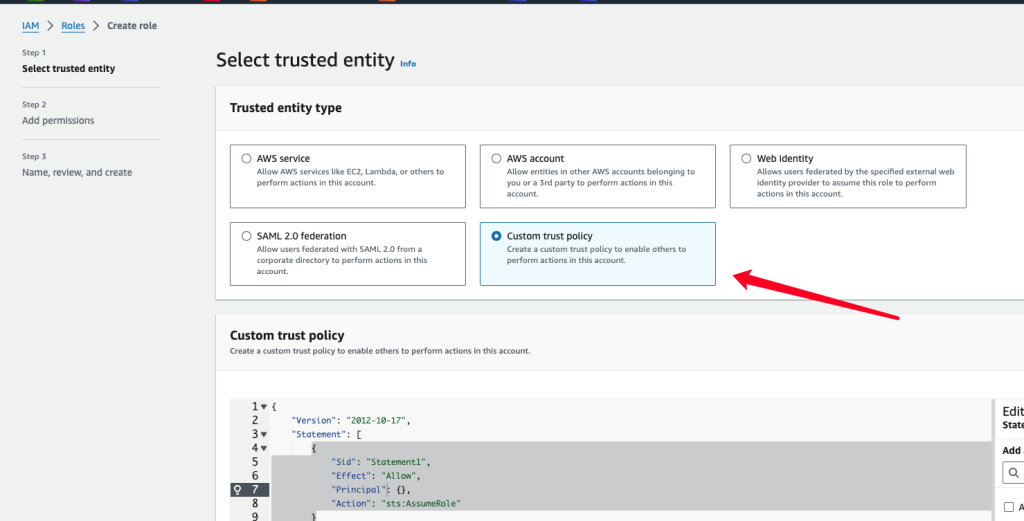
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::22223322:oidc-provider/oidc.eks.ap-southeast-1.amazonaws.com/id/BF92DE864F226E8B78D7D02695124817"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.ap-southeast-1.amazonaws.com/id/BF92DE864F226E8B78D7D02695124817:aud": "sts.amazonaws.com",
"oidc.eks.ap-southeast-1.amazonaws.com/id/BF92DE864F226E8B78D7D02695124817:sub": "system:serviceaccount:kube-system:aws-node"
}
}
}
]
}4. 创建好了新Role,然后就需要create inline policy
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:AssignIpv6Addresses",
"ec2:DescribeInstances",
"ec2:DescribeTags",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeInstanceTypes"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:*:network-interface/*",
"Effect": "Allow"
}
]
}5. 最后就是把这个role绑定到VPC CNI当中就完成了!
![]()
Facebook评论